Before we attack an enemy it is best to know them first, that way we would discover their weaknesses and attack them in the unguarded places. Information gathering becomes an inseparable activity in ethical hacking. Good information gathering may lead to a successful pen test or a failed one. It include three basic steps which is Footprinting, Fingerprinting and Enumeration.
Footprinting:

Footprinting is the blueprinting of the security profile of an organization, in a methodological manner.
The attacker may choose to source the information from:
- A web page (save it offline, e.g. using offline browser such as Teleport pro
- Yahoo or other directories. (Tifny is a comprehensive search tool for USENET newsgroups.
- Multiple search engines (All-in-One, Dogpile), groups.google.com is a great resource for searching large numbers of news group archives without having to use a tool.
- Using advanced search (e.g. AltaVista),
- Search on publicly trade companies (e.g. EDGAR).
- Dumpster diving (To retrieve documents that have been carelessly disposed)
- Physical access (False ID, temporary/contract employees, unauthorized access etc)
Fingerprinting:

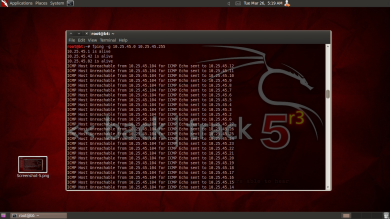
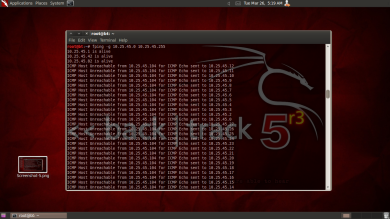
Fingerprinting is “guessing” a target operating platform.
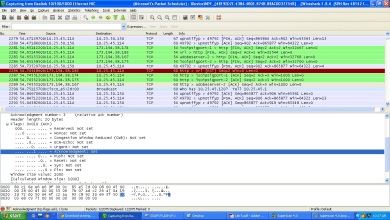
There are two type of fingerprinting which is the Active and Passive. Active fingerprinting is more accurate than passive but it leaves a visible track so it’s more dangerous to use it than the passive one.
Active fingerprinting is actively determining the target network OS by sending packets and examining its response. Passive fingerprinting is instead of relying on scanning the target host, passive fingerprinting captures packets from the target host and study it for signs that can reveal the OS.
The attacker may choose to source the information from:
- TTL – What the operating system sets the Time To Live on the outbound packet
- Window Size – What the operating system sets the Window Size at.
- DF – Does the operating system set the Don’t Fragment bit?
- TOS – Does the operating system set the Type of Service, and if so, at what?
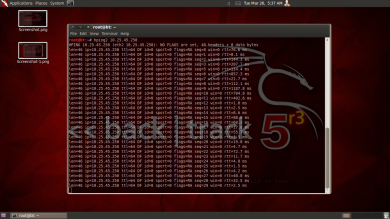
Enumeration:

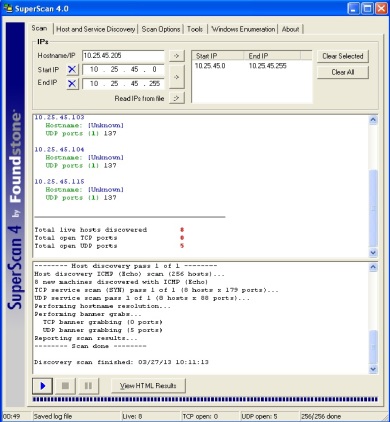
Enumeration is identifying valid user accounts or poorly protected resource shares.
The type of information enumerated by intruders:
Network resources and shares
Users and groups
Applications and banners
Source:http://www.amarjit.info/2010/03/what-is-footprinting-fingerprinting.html